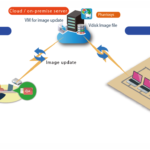
Essential tool for Managed Services
A simple-to-use yet advanced concept for managing computers and systems, that can be operated by fewer, entry-level IT personnel.
Cost-effective Managed Services
Managing networks of computer systems is a challenge for any IT department (or outsourced MSP), and an expensive bill for most organizations. Phantosys enables unprecedented benefits of centralized and unattended client system management.
No matter how many hundreds or thousands of computers, all can be managed as a single computer or “master system”, which every change can be automatically synced to all computers even if currently in use.
With much less need for time-consuming, repetitive, individual interventions, that often require displacement and logistics, your IT staff can be reduced or employed on more relevant tasks.
Data protection and access control
Protect sensitive data and Intellectual Property, with virtual disk technology, disk lock and port blocking features.
Complete control for improved data security
PATENTED DISK STORAGE FORMAT
With AES256 encryption, to avoid the risk of raw data loss in the event of hard drive loss/theft/scrap.
PORT/MEDIA BLOCKING
Block connection of USB/DVD/Wifi/SATA and other ports and media, to avoid the risk of data leakage or malware contamination.
CENTRALIZED DISK-LOCK CONTROL
Manage offline access policy to the entire disk or specific Vdisk instances with sensitive data, to prevent loss or data theft. Unique security feature for Laptops.

Reliable Backups and Instant recovery
Keep backups of entire systems and data disks always ready for instant recovery. Disk snapshots can be stored on client and server.
Exclusive technology of disk snapshot and recovery
Restoring backed-up files can take a long time to fully recover a user’s system and data. What if several users are affected simultaneously? Phantosys disk snapshot and recovery function can fix security incidents and immediately restore system and data, for one or many users.
Phantosys instant recovery requires only a reboot to get the user up and running again, and it’s also a great tool for the IT support to easily identify root-cause hardware issues and quickly act on the solution.